
Using TWS or Bluetooth devices? Here's how you can safeguard yourself from Bluetooth hacking - India Today

Blurtooth una vulnerabilidad de BT que permite a los hackers conectarse a dispositivos cercanos | Desde Linux

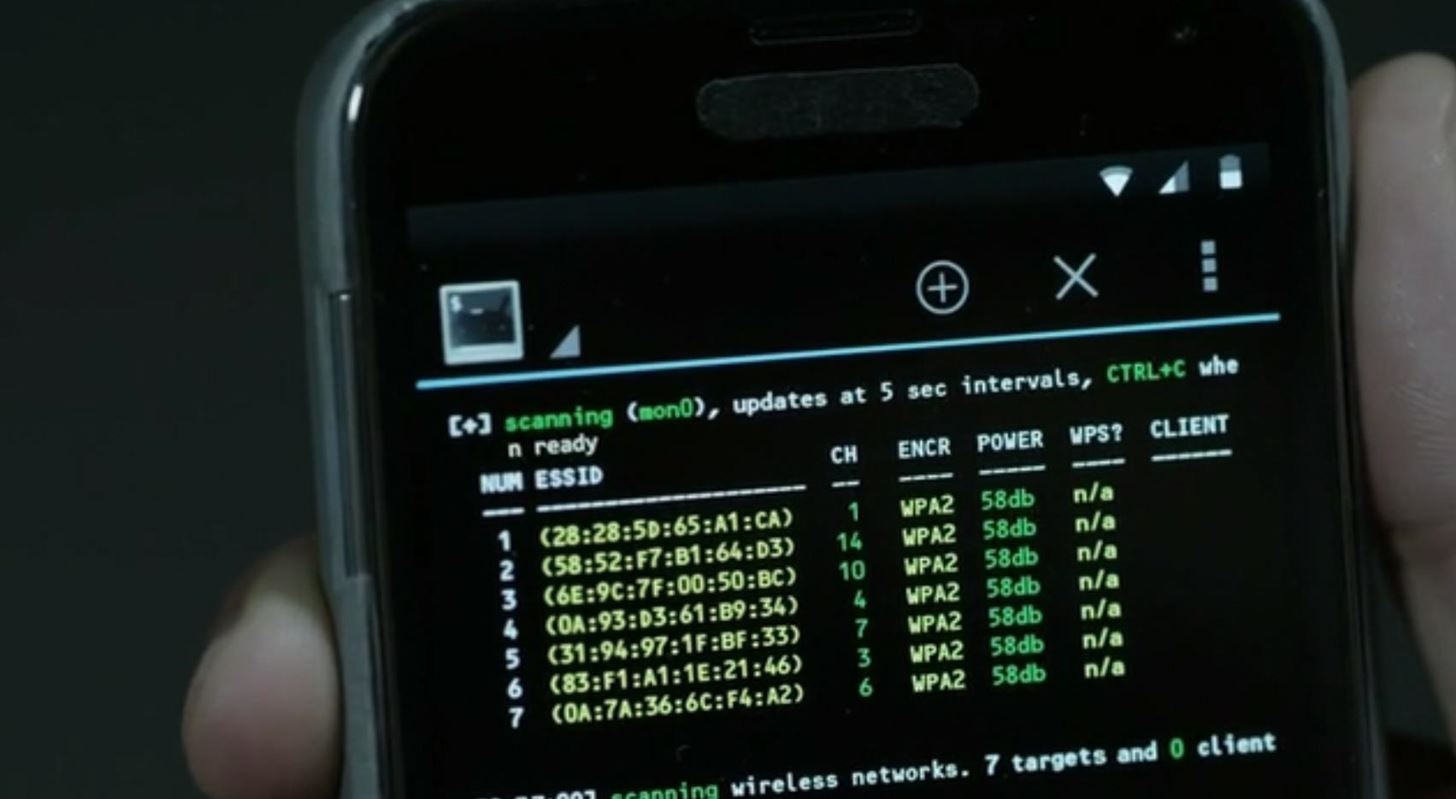
Which of the following Bluetooth hacking techniques refers to the theft of information from a wireless device through Bluetooth? | Infosavvy Security and IT Management Training

Diferencias entre los principales ataques por bluetooth: Bluesnarfing, Bluejacking y Bluebugging | Computer Hoy











/cdn.vox-cdn.com/uploads/chorus_asset/file/18316592/acastro_190717_1777_bluetooh_0001.jpg)





![How to Stop Bluetooth Hack on Phone [PDF] | BitVPN Blog How to Stop Bluetooth Hack on Phone [PDF] | BitVPN Blog](https://www.bitvpn.net/blog/wp-content/uploads/2020/03/phone-get-hacked-through-bluetooth-1024x536.png)


